SecureForge is a scam
How I uncovered a highly polished gray mail "vulnerability disclosure" phishing site.
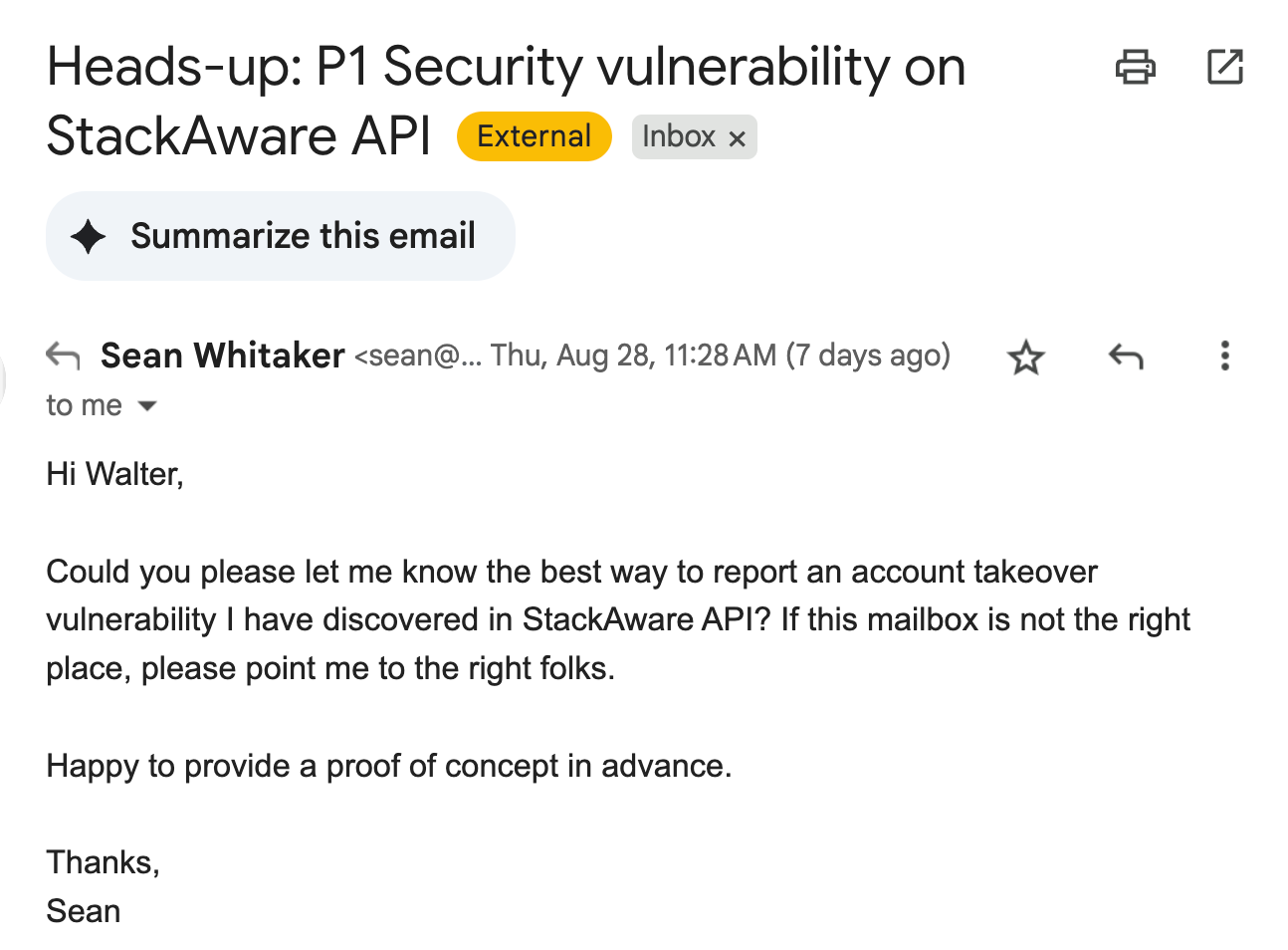
"Heads-up: P1 Security vulnerability on StackAware API"
👆 subject line of an email I got on August 28th.
This email, allegedly from "Sean Whitaker" at SecureForge, got my attention.
And raised suspicions.
"Sean" asked how "to report an account takeover vulnerability I have discovered in StackAware API."
Two things were strange:
I've never heard of an account takeover for an API.
StackAware has a public security.txt file.
An experienced ethical hacker would have gone there and found our vulnerability disclosure program (VDP).
Wanting to act in good faith in case he was legit, I directed him to our VDP.
6 minutes later, he replied, making my spidey senses tingle even more: "Quick question, do you offer any form of compensation or bug bounty rewards for high impact security vulnerabilities like this one?"
The obvious answer, if you read our VDP, is no.
We love ethical hackers and work with many good ones, but StackAware is a bootstrapped startup and cannot afford bug bounties (yet).
The fact he ignored our VDP and quickly asked about compensation raised another red flag.
So I started investigating.
If you go to secureforge [dot] io1 (archive.org version here, for when they inevitably get taken down), at first glance it 𝘭𝘰𝘰𝘬𝘴 kind of legitimate. But dig deeper and find:
They claim to be trusted by "500+ enterprises"
The only way to contact is a complex form
None of the buttons on the website work
They also claimed to be "Securing Digital Infrastructure Since 2015," but their site was registered in July 2025.
They even have an FAQ page that says:
"SecureForge is a registered security firm with verifiable credentials. You can verify our legitimacy through our CVE contributions, OWASP membership, client testimonials, and professional certifications."
"SecureForge OWASP" has no relevant Google hits.
Neither does the query "SecureForge CVE."
Testimonials are from real people, but...
...I saw a LinkedIn post by one of them, Nacho García Egea, claiming he never made the endorsement!2
That put the nail in the coffin.
I don't know what "Sean" planned next, but expect it would be something along the lines of "pay us or we won't give you the [non-existent] vulnerability."
So I used the "Report phishing" function on Gmail and reported the domain to Google.
This is unfortunately a fairly common approach, whereby unethical hackers attempt to "gray mail" companies into paying up.
Which makes clear disclosure policies key - they let you identify bad actors quickly.
Recommendations
Verify everything, especially if it seems urgent
Have a vulnerability disclosure program (VDP)
Be clear whether you pay (or not!)