The Chinese Government was probably responsible for the 2022 LastPass hack
A speculative attribution.
The stunning revelation that an unidentified malicious actor stole the encrypted vaults of more than 25 million LastPass customers ended 2022 on a panicked note for many.
I won’t go too much in to depth on the details of LastPass’ alleged technical shortcomings, but will recommend this post for an overview of them. And I would certainly recommend that you take appropriate action such as changing any passwords stored in your manager at the time of the breach.
What I am going to do here, however, is speculate on who as responsible for the hack. While all of my evidence is circumstantial, I have moderate confidence that it will eventually become clear the Chinese government is to blame.
I have 4 main reasons:
LastPass is a logical target for the Chinese government and its data would enhance existing stolen information
Over the past 15 years or so, Chinese military and intelligence services have waged an unprecedented campaign to steal data from the rest of the world. Much attention has focused on the theft of intellectual property, in what a former National Security Agency director called the “greatest transfer of wealth in history.”
In a separate effort, Chinese-directed and -backed cyber actors have also stolen incredible amounts of biographical, financial, travel and other data about Americans. This has occurred via events such as the:
Massive breach in 2014 of 500 million people’s personal and travel records from Marriott's Starwood hotel chain. Press reporting from unnamed U.S. government sources identified the culprits as being linked to the Chinese Ministry of State Security (MSS).
Successful infiltrations in 2014 and 2015 of the U.S. government’s Office Personnel Management (OPM). Attackers stole information on more than 20 million people associated with security clearance investigations and more than 1 million fingerprint sets from clearance holders. Media reporting has alternatively suggested either the MSS or Chinese military was responsible.
Attack against the credit monitoring firm Equifax in 2017 that resulted in the exfiltration of 147 million Americans’ personal information. The U.S. Department of Justice formally accused the Chinese military of the hack.
What is even more astounding is that fact that these are only the highest profile events that are reasonably associated with Chinese state actors. There are almost certainly additional breaches that have never been discovered or could not be conclusively linked to Chinese military or intelligence services.
For example, events such as the 2014 theft of 78 million people’s records from the health insurer Anthem likely belong with the preceding three but there is no publicly-available information tying them to Chinese state actors.
While the biographical, behavioral, and psychographic data that technology companies such as Meta and Google collect on their users is certainly vast and worthy of scrutiny, I believe it pales in comparison to what the Chinese government now maintains.
And that would make a centralized repository of Americans’ passwords an incredibly valuable target. By subsequently - and clandestinely - accessing the email, financial, medical, and other accounts of millions of U.S. citizens, the Chinese government could enrich its existing data sets to a nearly unimaginable extent.
The Chinese government has (or soon will have) the technical ability to decrypt LastPass vaults and the patience to do so
The Chinese government is both relentless and diligent in its efforts to crack American networks. The attack against LastPass required multiple successful infiltrations and lateral movements within the company’s network.
Furthermore, any cybercriminals planning an attack against LastPass - assuming they believed the company’s statements regarding its Zero Knowledge Architecture - would know that at best they would only recover encrypted vault data. The passwords contained within would not be immediately usable for follow-on attacks.
So one of four things happened:
The attackers went after the company for other reasons than the vaults but stole them as “targets of opportunity.”
The attackers didn’t believe LastPass’ security claims, expected to steal unencrypted vaults, and were financially motivated.
The attackers believed LastPass’ security statements, targeted the vaults, had a plan to crack them, and were financially motivated.
Same as #3, except the attackers were not financially motivated.
For #1, the data exfiltration operation seems like it was a major undertaking due to the massive quantity of data stolen. Thus, it was probably not a spur of the moment effort to exploit a target of opportunity. Additionally, it’s not clear what else of value LastPass would have aside from its customers’ vaults to motivate an attack in the first place.
For #2 and #3, cyber criminals motivated solely by money are highly unlikely to go after “hard targets” (which I consider LastPass to be) without a large and immediate financial incentive. Although there may have been holes in LastPass’ security, there are undoubtedly easier targets from which you can financially valuable data. And the company convincingly explained that customer vaults would require at least some effort to decrypt if stolen.
Thus, Occam’s Razor would strongly point to #4 as the most likely situation.
And since the modus operandi of the Chinese government is clear from previous incidents, they are the most likely candidate of the competing non-financially motivated suspects (Russia, Iran, et. al.).
This is also because the Chinese government is aggressively investing in quantum computing specifically to crack encrypted data. In fact, analysts have warned (before the full extent of the LastPass hack became public) that the Chinese government might steal encrypted data now to decrypt it later!
Financially-motivated actors would have struck quickly to rob those they could
While it’s not clear exactly when the vaults were stolen from LastPass, it could have happened as early as August 2022.
And although there is no way to prove this, I speculate that at least 1 out of the 25 million users of LastPass used easily-crackable passwords, e.g. less than 12 characters and/or using obvious words, phrases, or sequences. This situation probably describes more than 4% of users considering that 24-83% of Americans use weak passwords of some type per various reports.
I will grant, though, that people using password managers are probably more security savvy than the average American, so 4% seems like a conservative number. Additionally, I know that not all LastPass users are Americans but it seems safe presume many if not most are due to the company’s U.S. headquarters and data residency policy for personal users.
Thus, the LastPass attacker would rapidly (between seconds and days per this chart) be able to recover the full password inventories of hundreds of thousands - and possibly millions - of people.
Assuming the attacker were financially-motivated, it would have a very strong incentive to exploit this information immediately before people became aware of the breach and began revoking their credentials.
So if all the threat actor wanted was money, we should have seen a massive wave of fraud, theft, and other “noisy” malicious activity in the late summer and fall of 2022. Stealing money or identities usually gets people’s attention quickly and such a spasm of cybercrime almost certainly would have triggered affirmative action on the part of banks, credit reporting agencies, and other stakeholders. And we probably would have heard about it in the media.
Since this didn’t happen, I presume the LastPass attacker had something else in mind.
There is speculation that LastPass’ digital supply chain had Chinese government-linked elements
This is probably the weakest piece of evidence, but I am including it for completeness.
After reviewing a message board discussion about LastPass and its security (from prior to the hack), I noticed the below comment:
Note: names removed from my screenshots in case these people want to “re-anonymize” themselves at some point in the future.
I was unable to identify the “response from LogMeIn” (owner of LastPass at the time of the post, but not the breach). But this post implies that the company’s digital supply chain included certain Chinese “covered telecommunications products or services.”
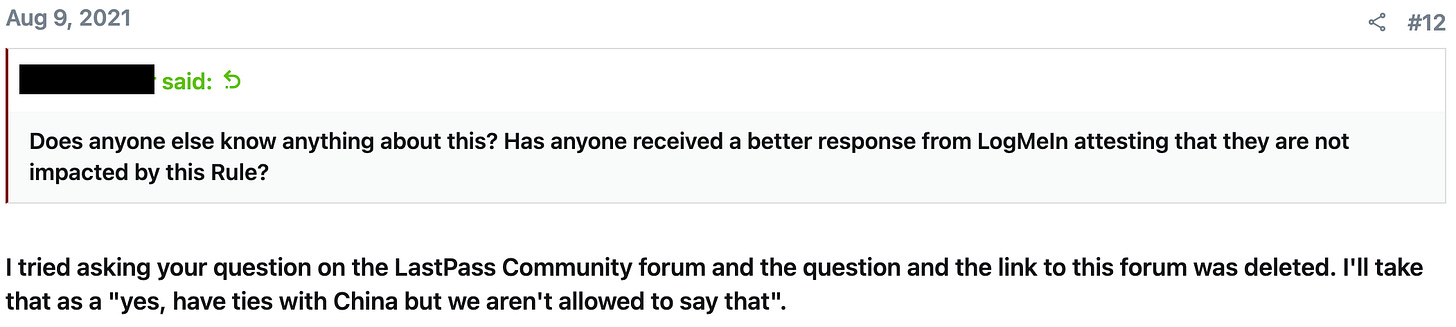
The below response (from a separate username) to the original post was also intriguing:
So while far from a smoking gun, it seems plausible that one or more third parties upon which LastPass relied had ties to Chinese government-backed technology companies. And this would make a supply attack via one such entity more plausible.
Conclusion
Based on these four points, I am reasonably confident in my assessment that Chinese government-backed or -directed actors stole the vaults of 25 million+ LastPass customers.
I want to reinforce my earlier point that my assessment is based strictly on circumstantial evidence and that I may quite well be mistaken. The complete password inventories of millions of people represent an enticing target for all manner of cyber criminal groups, and it could have been any one of them.
I will consider updating this post as more information becomes available and will make a note if someone makes a convincing attribution to another entity.
In the meantime, though, update your threat model accordingly.
Disclosures: I was a LastPass user personally impacted by the breach discussed (and have migrated to another competing product). I was also impacted by the 2014/2015 OPM hack and 2017 Equifax attack.