Set up CISA Cyber Hygiene and put it on autopilot
The good, the bad, the ugly.
TL;DR
Identify the interning-facing static IPv4 addresses to be scanned in one of the following formats: CIDR notation (e.g. x.x.x.0/24), IP range (e.g. x.x.x.1-x.x.x.200), or individual IPs (e.g. x.x.x.1) with one entry per line.
If any of these are hosted by a third party (cloud provider, SaaS application), ensure you notify them about or get permission (whichever is required by your agreement with them) for conducting the scanning.
Email vulnerability@cisa.dhs.gov with the subject line “Requesting Cyber Hygiene Services.” Add the following information to the email:
Entity name:
HQ address:
Point of Contact (POC) Name:
POC Email:
POC Phone:
How did you hear about us?:
Complete the Assessments Service Request Form and Cyber Hygiene Acceptance Letter.
If you are going to complete the steps below to automate the process, then make sure your “distro email” is one that you can integrate with Zapier.
You will be emailed a password. Store it in a password manager and, if desired, integrate it into your Zapier workflow (requires paid plan).
Receive and take action on the reports emailed to you. If you want to automate the process, follow the below steps.
Set up Zapier Automation to process report and alert you to scan results (optional)
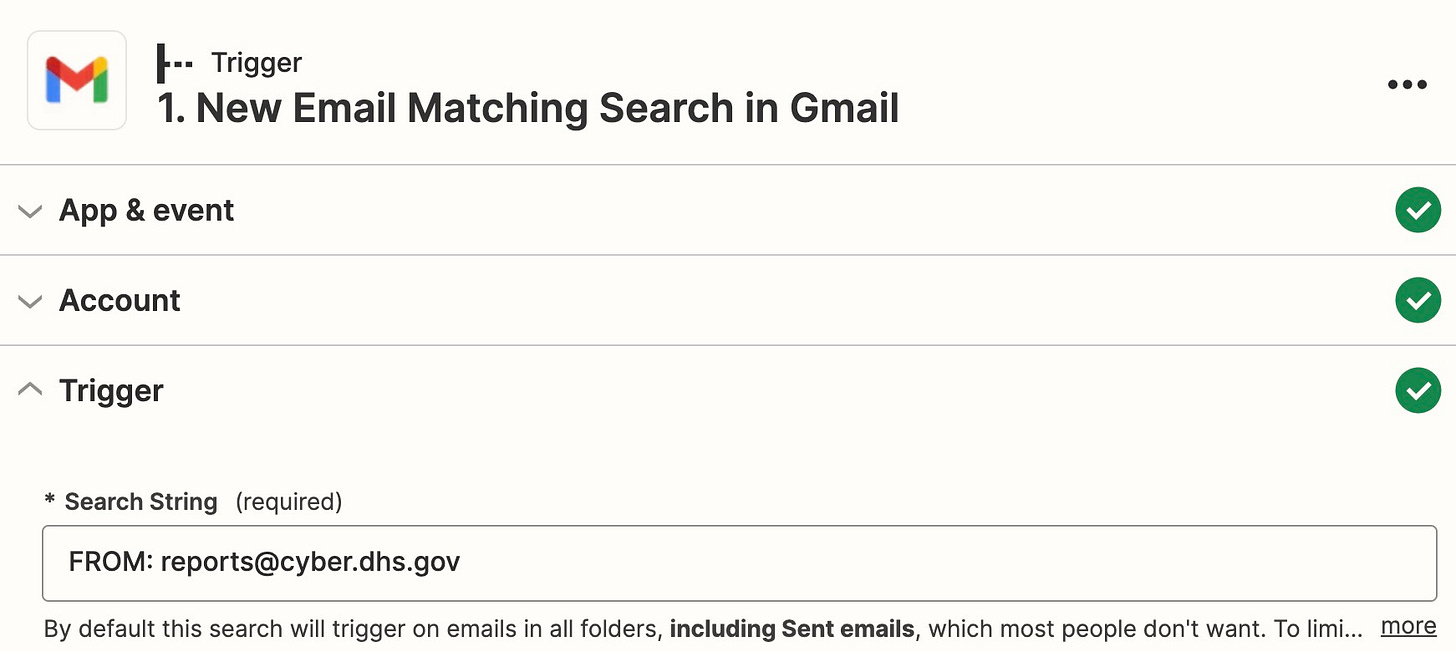
Your trigger should be “New Email Matching Search in Gmail,” and the search field should be “FROM: reports@cyber.dhs.gov.”
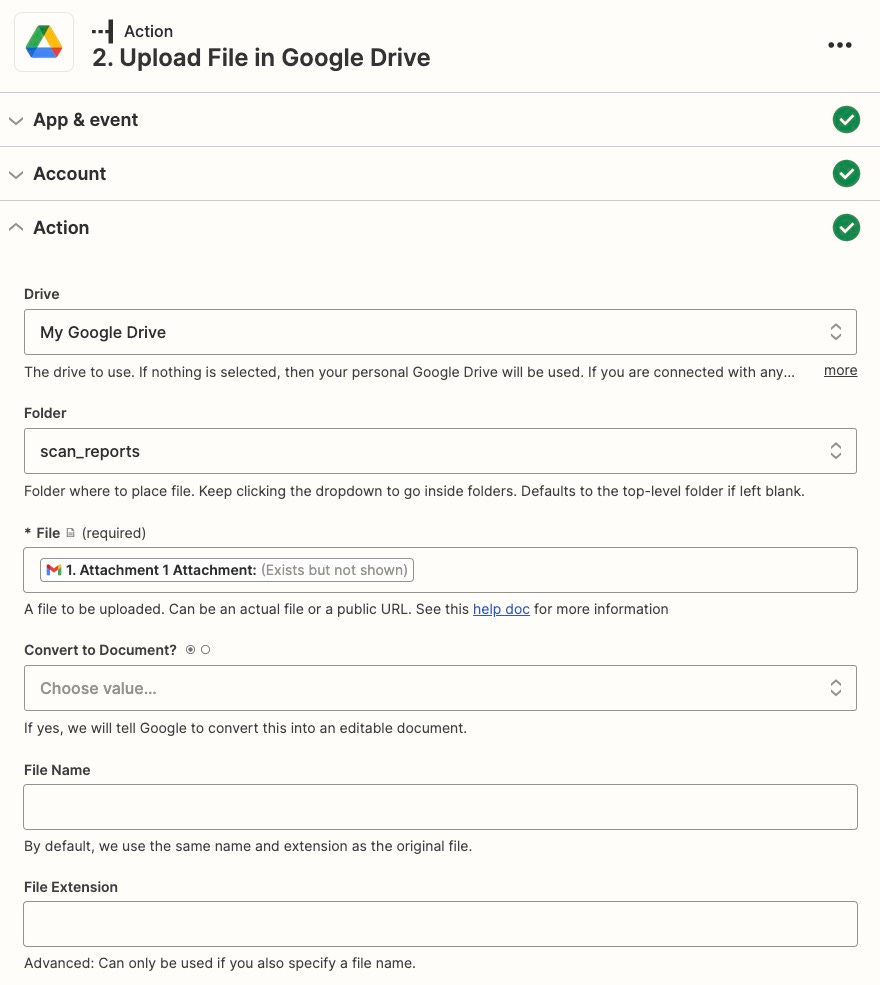
The next action should be “Upload File in Google Drive.”
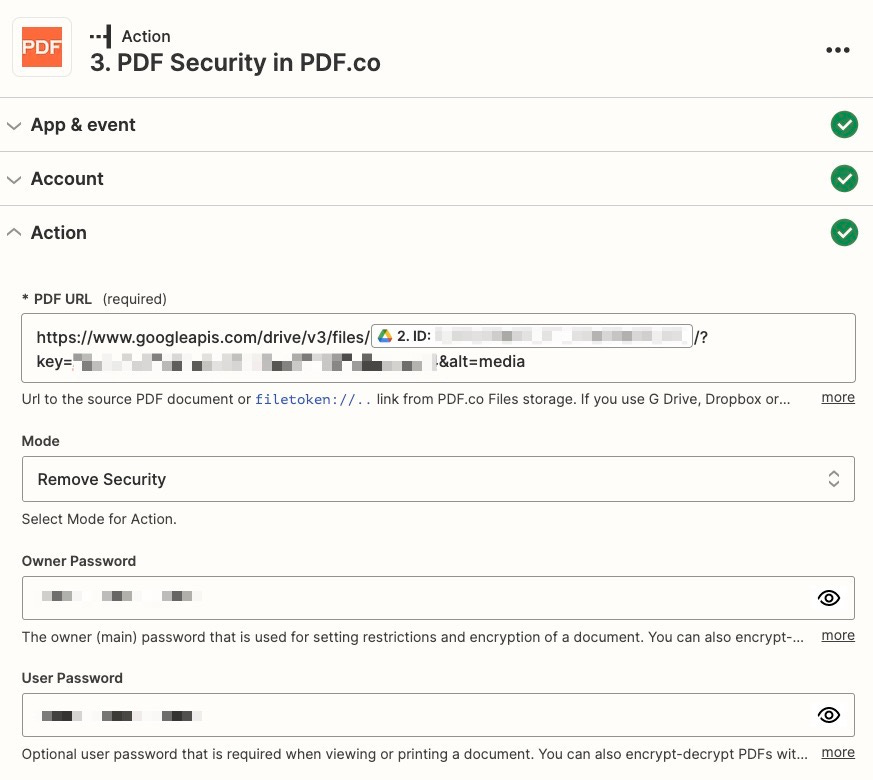
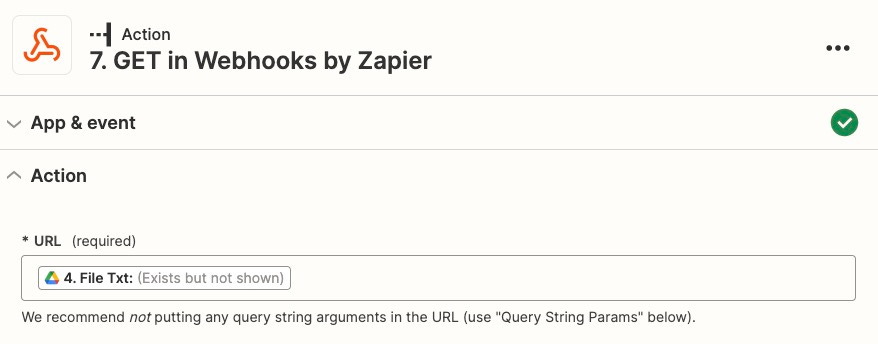
Select PDF.co as the next action, and select “PDF Security” as the event. WARNING: please read the security considerations section below.
Dynamically set the URL you will call based on the ID from step 2. See this StackOverflow post for details, but the URL should be https://www.googleapis.com/drive/v3/files/file_id_from_previous_step/?key=google_drive_api_key&alt=media. You will need to generate a Google Drive API key, following these steps.
Set “Mode” to be “Remove Security” and set the “Owner Password” and “User Password” to your CISA-provided value.
“Upload File in Google Drive” and convert to a Google Doc so you have a record of it.
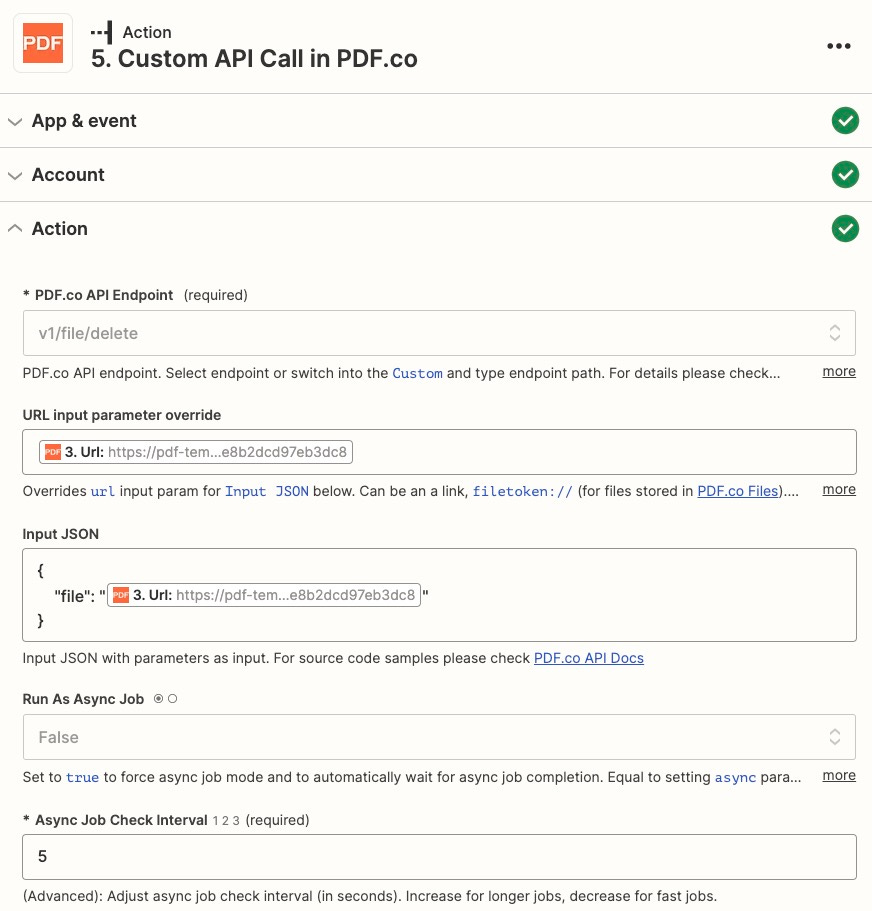
Delete the temporary file using an API call to PDF.co.
Now find your new Google Doc.
Due to a quirk in Zapier, you’ll need to use the Webhooks App to get the full text.
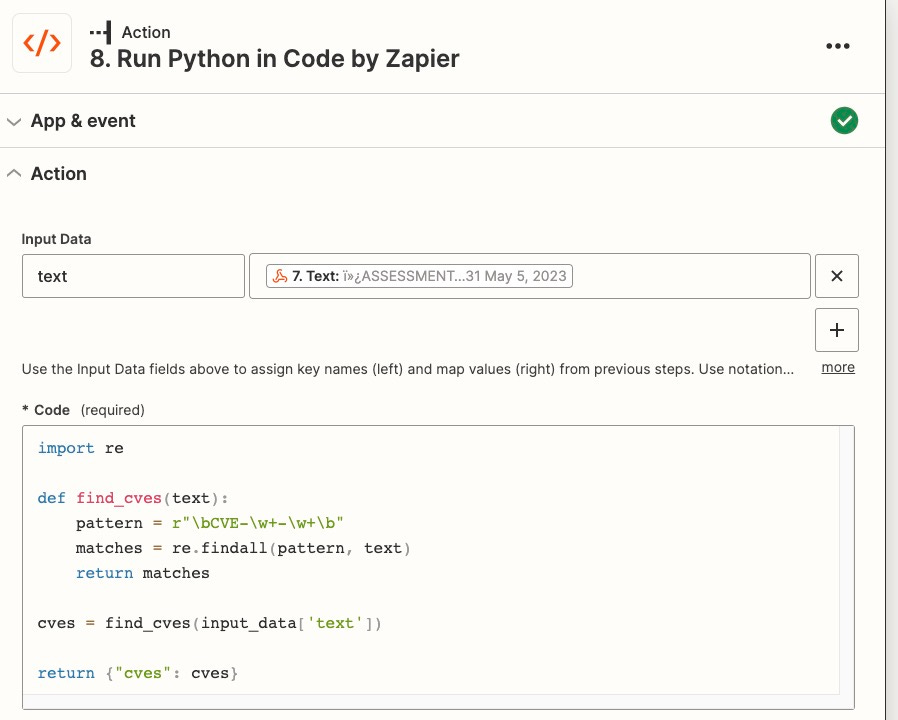
Use the below code to extract any CVEs from the report:
import redef find_cves(text):pattern = r"\bCVE-\w+-\w+\b"matches = re.findall(pattern, text)return matchescves = find_cves(input_data['text'])return {"cves": cves}Send an email to yourself or your security distribution list with the results. Note: if your security email inbox is an alias of your personal email, any emails you send to yourself will be marked as read because Gmail treats the sent and received emails as a single object. There is no way to mark as unread with a Gmail filter, thus, you should probably just send it directly to yourself.
If you want to get really crazy, you could look up the Exploit Prediction Scoring System (EPSS) rating via the free API or even create a vulnerability instance in StackAware, but even I haven’t gone that far yet.
Requirements
Discussion
The Cybersecurity and Infrastructure Security Agency (CISA) cyber hygiene program is essentially a combination of nmap host identification and Nessus vulnerability scanning, done for free as a public service. Details are here, but it’s open to basically anyone, including for-profit organizations.
Unless you are already running some sort of attack surface management tool, it probably makes sense to get this set up ASAP. And although you should check with a lawyer on this point, you could probably require your vendors to contractually submit to this scanning as well and add you to the distribution list of reports that are generated (assuming the vendors agree). This makes it something of a “poor man’s” third-party risk monitoring tool.
Implementing the automation is of course your choice, but CISA doesn’t provide this data via REST API.
Security considerations
The information CISA provides is not especially sensitive as it can be legally obtained by anyone with a vulnerability scanner and knowledge of your IPv4 addresses. Thus, I do not consider the risk of using Zapier and PDF.co to be prohibitive.
The primary risk I see is not being alerted to known vulnerabilities in your network, not an attacker taking an incredibly circuitous path to obtain this information by hacking a third party. With that said, I have provided a quick risk assessment for both companies below.
Zapier
Mature security
U.S.-based
SOC 2 and SOC 3 attestations
Maintains paid bug bounty program
24/7 on-call security team
PDF.co
Moderately mature security
U.S.-based (at least the corporate entity is)
Detailed security page but no attestations for service
Maintains well-documented but unpaid vulnerability disclosure policy.
Will create a temporary copy of your .pdf available on the open internet, available without authentication (by default on the lower tier plans, this is deleted after 1 hour). You can immediately remove it using the API call step I detail above. While I acknowledge there is a small window of time where someone could grab your document, without password protection
CISA Risk Rating System
Although I think CISA cyber hygiene is overall a good program, there is one aspect that I must critique: CISA’s “Risk Rating System” (RRS).
The Risk Rating System (RRS) emphasizes higher-rated CVSS scores to ensure that hosts with a large number of lower-risk vulnerabilities do not outweigh hosts with a smaller number of high-risk vulnerabilities, while ensuring that hosts with an extreme number of low-risk vulnerabilities are not overshadowed by hosts with a single higher-risk issue. The RRS also ensures that hosts with a significant number of high-risk vulnerabilities will not be overshadowed by a host with only a single critical vulnerability.
This rubric does not appear to be publicly-posted anywhere on CISA’s web site, and I believe it represents the 9th method of vulnerability prioritization used by the federal government.
Frankly it doesn’t make any sense.
This system begins with a flawed foundation by using CVSS and does even worse by implicitly suggesting CVSS represents risk (which the standard itself clearly states it does not). Unfortunately the RRS goes further by assigning completely arbitrary values to individual scores.
To quote Jack Jones, creator of the Factor Analysis of Information Risk (FAIR) method, the “CVSS scoring model involves a lot of math on ordinal values. Functionally, that’s the same thing as doing math on a color scale.”
Please, ignore this risk rating and use something like the EPSS instead.
I hope that you find Deploying Securely useful. If so, here are some more resources that can help:
1. My free, risk-based vulnerability management (VM) email course. Use it to build the foundation for a quantitative VM program in 5 days.
2. The Deploy Securely VM SOP. A template for running a program developed from years of real-world experience, it will save you huge amounts of time and effort.
3. StackAware’s 0 → 1 vulnerability management offering, which will get you immediate assistance in building your security program.